Introduction to Cryptography and the Caesar Cipher
Cryptography, the art of writing and breaking codes, has fascinated people for centuries. From ancient hieroglyphs to modern digital encryption, the quest to secure and decipher information has been a constant pursuit. The Caesar cipher, named after Julius Caesar who famously used it in his private correspondence, stands out as a cornerstone in the history of cryptography. This simple yet ingenious method involves shifting the letters of the alphabet by a fixed number, transforming the original message into a scrambled version, thereby keeping its contents confidential from unintended recipients. Although elementary by today's standards, the Caesar cipher marked a significant milestone in the evolution of cryptographic techniques. It embodies the basic principles of substitution and transposition, which are the foundation of more complex encryption methods. As we delve into the workings of this cipher, we begin to unravel the rudimentary concepts of cryptography and offer insights into how basic ideas can give rise to intricate systems of communication security. This exploration is not just a journey through a historic cipher, but a window into the vast and fascinating world of cryptography, where every encrypted message is a puzzle waiting to be solved.
Basics of the Caesar Cipher: How it works
At its core, the Caesar cipher is a study in simplicity and elegance in the field of cryptography. This encryption technique works on a basic principle: shifting each letter in the plaintext (the original message) a fixed number of positions down or up the alphabet. For example, with a shift of three positions, "A" becomes "D," "B" becomes "E," and so on, until the alphabet winds back around at the end. This shift, known as the key, is the cornerstone of encryption. It's both the tool for encryption and the secret for decryption.
The beauty of the Caesar cipher lies in its simplicity. Unlike modern encryption methods that require complex algorithms and large amounts of computing power, this cipher can be performed with just a pen and paper. However, its simplicity is also its vulnerability. The limited number of possible shifts (26 in the English alphabet) makes it susceptible to brute force attacks, where every possible key is tried until the message is deciphered. Nevertheless, understanding how the Caesar cipher works is crucial to understanding the basics of cryptographic methods. It illustrates the basic concept of shifting and substituting characters, a rudimentary technique that forms the basis of more advanced and secure encryption methods used in today's digital world. Through this simple cipher, we can appreciate the evolution of cryptography from basic alphabetic manipulations to the complex algorithms that secure our digital communications.
The Caesar Cipher: A step-by-step encryption process
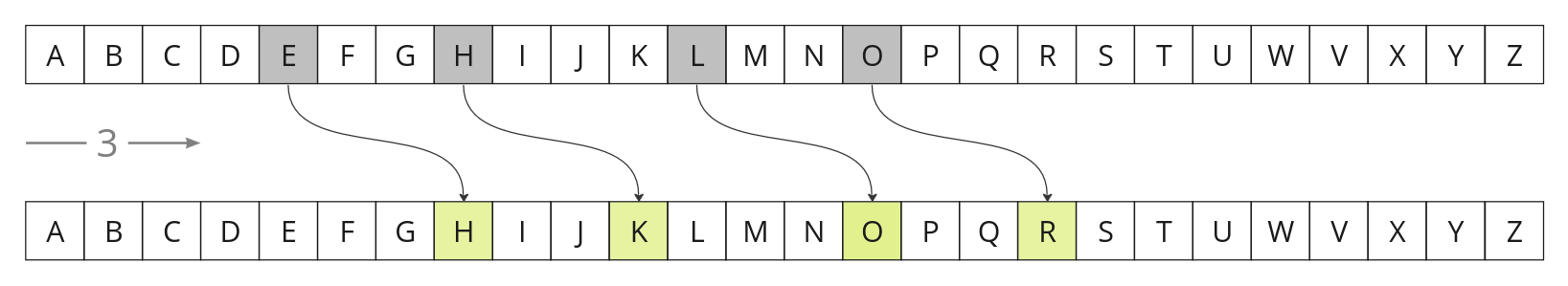
To fully appreciate the Caesar cipher, it's instructive to walk through its encryption process. This journey from plaintext to ciphertext is both a lesson in cryptography and a testament to the ingenuity of ancient codes. Let's break it down step by step, using a shift of three, a common choice in historical applications of this cipher.
- Choose the shift (key): The first step is to choose the shift number. For our example, we'll use a shift of three. This means that each letter in our message will be shifted three places down the alphabet.
- Prepare the plain text: Consider a simple message, such as "HELLO". This is the plaintext, the original message we want to encrypt.
- Apply the Shift: Now we apply our shift of three to each letter. "H" becomes "K", "E" becomes "H", "L" becomes "O", and so on. Each letter makes a small jump down the alphabet, landing three letters away from where it started.
- Generate the ciphertext: After moving each letter, our message "HELLO" becomes "KHOOR". This is the ciphertext - the encrypted version of our message, now cloaked in secrecy.
- Transmit the ciphertext: The ciphertext "KHOOR" can now be securely transmitted to a recipient. Without knowledge of the shift key, deciphering it will be a challenge for unintended readers.
- Decryption by the recipient: The recipient, knowing that the shift was three, simply reverses the process. They move each letter in "KHOOR" three places up the alphabet to reveal the original message, "HELLO".
This methodical transformation from plaintext to ciphertext and back again is the essence of the Caesar cipher. It demonstrates how a simple concept-shifting letters in the alphabet-can be used to create a veil of secrecy. While it may not withstand the sophisticated attacks of modern cryptanalysis, the Caesar Cipher serves as an excellent tool for introducing the principles of encryption and the art of secret communication.
Decoding the Mysteries: How to Decrypt a Caesar Cipher
Decrypting a Caesar cipher, the process of turning the ciphertext back into readable plaintext, is the reverse of the encryption process. It relies on the same key used for encryption and requires a simple, systematic approach. Here's how it's done:
- Understand the key: To decrypt a message, the recipient must know the shift key used for encryption. If the key is 3, the decryption process involves shifting in the opposite direction, three positions up the alphabet.
- Receiving the ciphertext: Consider a ciphertext like "KHOOR" that we need to decrypt.
- Reverse the Shift: Apply the reverse shift to each letter in the ciphertext. Since our key is 3, we shift each letter three positions back in the alphabet. "K" becomes "H", "H" becomes "E", and so on until every letter has been adjusted.
- Reveal the plaintext: After applying the reverse shift to each letter, the original message is revealed. In our example, "KHOOR" is decoded back to "HELLO".
- Interpreting the message: The recipient can now read and understand the original message as it has been successfully converted from its encrypted form.
The decryption of the Caesar cipher demonstrates the symmetry of cryptographic methods: the same rule applied in reverse undoes the encryption. This symmetry also points to the cipher's vulnerability - if an interceptor guesses the key, he can easily decrypt the message. This ease of decryption underscores why the Caesar cipher is more of a stepping stone to understanding cryptography than a robust tool for secure communication. However, it remains a perfect example for illustrating the basic principles of encryption and decryption, and serves as a foundational exercise for those venturing into the vast and intricate world of cryptographic science.
Variations of the Caesar cipher: Exploring Different Shifts
While the basic Caesar cipher involves a simple, fixed shift of the alphabet, exploring its variations can provide a deeper insight into the flexibility and adaptability of this ancient encryption technique. By varying the shift key, the cipher can be customized, making it slightly more difficult for unintended recipients to crack. Let's explore how different shifts can be applied and how they affect the security of the cipher.
- Different Shift Values: The classic Caesar cipher uses a shift of three, but any shift from 1 to 25 is possible. Each shift value creates a different encryption pattern. For example, a shift of 1 moves "A" to "B", "B" to "C", and so on, while a shift of 25 would wrap around the alphabet, moving "A" to "Z".
- Shift Direction: The direction of the shift, either forward or backward, can also be varied. A forward shift moves letters down the alphabet, while a backward shift moves them up. This variation adds another layer of customization to the cipher.
- Random shifts: In a more complex variation, each letter in the plaintext could be shifted by a different amount, perhaps determined by a secret pattern or rule known only to the sender and receiver. This approach greatly complicates the decryption process without prior knowledge of the pattern.
- Multiple Shift Ciphers: Another variation involves the use of multiple shifts in a single message. For example, the first half of the message might use a shift of 4 and the second half a shift of 7. This method would require the recipient to know the exact points of change and the corresponding shifts.
- Rotating Shifts: In a more advanced variation, the shift value changes after each letter is encrypted. For example, the first letter might be shifted by 1, the second by 2, the third by 3, and so on, cycling back after a certain number of shifts.
These variations show that even within the constraints of the Caesar cipher, there is room for creativity and increased complexity. While these modifications do not elevate the Caesar Cipher to the security level of modern encryption methods, they do provide an excellent playground for understanding basic cryptographic principles. Experimenting with different shifts and patterns not only adds a layer of intrigue to the cipher, but also serves as a bridge to more advanced concepts in the field of cryptography.
Strengths and limitations of the Caesar cipher
The Caesar cipher, with its long history and simple mechanics, presents a mix of strengths and limitations that offer valuable lessons in the broader context of cryptography.
Strengths:
- Simplicity: The most important strength of the Caesar cipher is its simplicity. It is easy to understand and execute, requiring no special equipment or advanced mathematical knowledge. This makes it an excellent educational tool for introducing the basic concepts of cryptography.
- Historical Significance: As one of the earliest known ciphers, the Caesar cipher has a rich historical context. It provides an entry point into the study of encryption and the evolution of cryptographic techniques over time.
- Foundation for More Complex Systems: Understanding the Caesar Cipher lays the foundation for learning more complex encryption methods. It embodies fundamental concepts such as substitution and shifting, which are at the core of many modern cryptographic algorithms.
Limitations:
- Vulnerability: The Caesar cipher is highly vulnerable to various forms of cryptanalysis, such as brute force attacks. Since there are only 25 possible shifts for the English alphabet, an interceptor can easily try each one and decrypt the message.
- Lack of Key Complexity: The key in the Caesar cipher (the shift number) is simple and lacks the complexity required by modern encryption standards. The lack of a robust key mechanism makes it impractical for any serious or secure communication.
- Predictability: Due to its linear and predictable nature, the Caesar cipher is susceptible to frequency analysis, where an attacker studies the frequency of letters or groups of letters in the ciphertext and compares them to known frequencies in the language.
While the Caesar Cipher is not suitable for securing sensitive information, especially in the digital age, its simplicity provides an accessible introduction to the principles of encryption. It serves as a stepping stone to more advanced cryptographic techniques and remains a fascinating and instructive aspect of the history of secret communication. The cipher's simplicity, combined with its vulnerability, provides a vivid example of the challenges inherent in designing secure encryption methods and the ongoing evolution of cryptography.
Simple Cryptography: The Caesar cipher in everyday life
The Caesar cipher, despite its simplicity and historical origins, still finds relevance in our everyday lives, particularly as a tool for basic encryption and educational purposes. Its straightforward mechanics make it accessible to a wide audience, from hobbyists to students, and stimulate interest in the larger field of cryptography.
- Educational Tool: The Caesar Cipher serves as an excellent introduction to cryptography in an educational setting. It helps students grasp basic concepts such as encryption, decryption, and the importance of keys in a tangible, hands-on way. By breaking and creating simple ciphers, students can explore the basics of secret communication and develop a foundation for understanding more complex encryption methods.
- Puzzle and Game Enthusiast's Delight: For puzzle enthusiasts and game designers, the Caesar cipher offers a simple yet intriguing challenge. It is often used in puzzle games, escape rooms, and scavenger hunts, providing a blend of historical intrigue and cryptographic challenge.
- Basic Security Measures: In scenarios where high-level security is not a concern, the Caesar cipher can still be used for basic encryption tasks. For example, it can be used to create simple passwords, to encode answers to trivia questions, or even in simple DIY projects where a rudimentary level of secrecy is desired.
- Cultural and artistic uses: The cipher often appears in cultural and artistic contexts, such as novels, movies, and television shows, usually as a plot device or to add an element of mystery. Its historical significance and ease of understanding make it an attractive choice for storytellers and artists.
- Introduction to Coding and Algorithmic Thinking: For budding programmers and computer enthusiasts, the Caesar cipher serves as a gentle introduction to the concepts of algorithms and coding. Implementing the cipher in a programming language can be a beginner-friendly project that combines historical knowledge with practical coding skills.
The continued relevance of the Caesar cipher in everyday life underscores the enduring fascination with codes and secret communication. It bridges the gap between ancient cryptography and modern encryption techniques, illustrating the evolution of secret messages from parchment to pixels. While it may no longer be suitable for protecting state secrets, its legacy lives on as a tool for education, entertainment, and an introduction to the world of cryptography.
Comparing the Caesar cipher with other encryption techniques
To appreciate the place of the Caesar cipher in the broad spectrum of encryption, it's instructive to compare it to other encryption techniques, both ancient and modern. This comparison not only highlights the evolution of cryptographic methods, but also underscores the advances in security and complexity that have become essential in the digital age.
- Substitution Ciphers: Like the Caesar cipher, simple substitution ciphers replace each character in the plaintext with a different character. However, instead of a uniform shift, substitution ciphers use a more complex system where each letter is mapped to a different, seemingly random letter. This increases security over the Caesar cipher, but remains vulnerable to frequency analysis.
- Transposition ciphers: Transposition ciphers, another form of classical encryption, differ from the Caesar cipher by rearranging the order of the letters in the plaintext rather than substituting them. This method creates a completely different level of complexity, but can be combined with substitution methods for increased security.
- Vigenère Cipher: An evolution of the Caesar cipher, the Vigenère cipher uses a series of different Caesar ciphers based on the letters of a keyword. This polyalphabetic method greatly increases the complexity and security of the cipher, making it less susceptible to simple cryptanalysis.
- Modern Symmetric-Key Encryption: Modern methods such as AES (Advanced Encryption Standard) use symmetric keys, where the same key is used for both encryption and decryption. These techniques involve complex algorithms that operate on binary data, making them far more secure than the Caesar cipher and suitable for encrypting large amounts of data quickly.
- Public-Key Cryptography: Unlike the Caesar cipher, which uses the same key for encryption and decryption, public-key cryptography uses two different keys - a public key for encryption and a private key for decryption. This method, which includes algorithms such as RSA, is fundamental to secure communications over the Internet, including file transfer and digital signatures.
Comparing the Caesar cipher to these more advanced techniques highlights its simplicity and the tremendous advances that have been made in cryptographic practice. While the Caesar cipher laid the groundwork for understanding basic encryption concepts, modern methods have extended these principles to meet the demands of secure communication in an increasingly digital world. The evolution from simple character shifting to complex algorithms reflects both advances in computing power and the ever-growing need for stronger, more secure cryptographic solutions.
Getting Hands-On: Interactive Exercises with the Caesar Cipher
Engaging with the Caesar Cipher through interactive exercises is not only a fun way to understand its mechanics, but also a practical approach to grasping the basic concepts of cryptography. These exercises can range from manual encryption and decryption to creating basic programs that automate the cipher process. Here are some interactive activities that can deepen your understanding of the Caesar cipher:
- Manual Encryption and Decryption: Start with a simple exercise to manually encrypt and decrypt messages using the Caesar cipher. Choose a key and a message, then use the cipher to encrypt and decrypt it. This hands-on approach will help you understand the basic mechanics of the cipher.
- Breaking the Cipher: Try to break a Caesar cipher without knowing the key. This can be done by frequency analysis or by trying all possible shifts. This exercise provides insight into the weaknesses of the cipher and introduces basic cryptanalysis techniques.
- Programming the Cipher: For those with programming skills, writing a simple program to perform encryption and decryption of the Caesar cipher can be a rewarding task. This not only reinforces the understanding of the cipher, but also provides a practical introduction to applying programming skills to cryptography.
- Explore variations: Experiment with variations of the Caesar cipher, such as using different shift values, reverse shifting, or even developing a pattern for shifting. This can be a creative exercise in understanding how small changes can alter the encryption process.
- Group Exercises: Working in groups, you can encrypt a message using the Caesar cipher and have others try to decrypt it. This collaborative exercise can be a fun way to engage with the cipher and understand its practical implications in a group setting.
- Historical Contextualization: Research and discuss the historical use of the Caesar cipher and other ancient ciphers. Understanding the context in which these ciphers were used can provide a deeper understanding of their significance and limitations.
These interactive exercises provide a hands-on approach to learning about the Caesar cipher, moving beyond theoretical understanding to practical application. They serve not only as educational tools, but also as a bridge to more advanced concepts in cryptography, providing insight into the intricacies and challenges of secure communications.
The Future of Simple Ciphers in the Age of Advanced Cryptography
In an era dominated by complex encryption algorithms and sophisticated cyber threats, the role and future of simple ciphers like the Caesar cipher may seem unclear. However, these basic cryptographic methods are still relevant in several ways, particularly in education and conceptual understanding of cryptography.
- Educational Value: The Caesar cipher and similar simple ciphers serve as basic teaching tools in cryptography. They provide a clear and tangible way for students and beginners to grasp the basic principles of encryption and decryption, laying the foundation for understanding more complex systems.
- Conceptual Understanding: Simple ciphers embody the basic concepts of cryptography, such as key management, the importance of secrecy, and vulnerability to various types of attacks. Learning about these ciphers provides a historical perspective on how encryption methods have evolved to meet increasing security challenges.
- Introduction to Algorithmic Thinking: For individuals learning programming or algorithmic problem solving, implementing simple ciphers like the Caesar cipher is an excellent exercise. It bridges the gap between theoretical concepts and practical application, fostering logical thinking and coding skills.
- Cultural and recreational use: The Caesar cipher continues to find a place in cultural and recreational contexts, such as puzzle solving, games, and storytelling. Its simplicity and historical context make it appealing for these purposes.
- Inspiring Security Awareness: In an age where data security and privacy are paramount, understanding the basics of ciphers like the Caesar Cipher can be a stepping stone to appreciating the importance of robust encryption in everyday digital interactions.
- Ongoing Relevance to Cryptography Studies: As a historical artifact and a fundamental example of substitution ciphers, the Caesar Cipher remains a topic of interest in the study of cryptography. It serves as a reminder of the origins of the field and the continuing evolution of encryption techniques.
In conclusion, while simple ciphers like the Caesar cipher are no longer used to secure sensitive information, they continue to play an important role in education, cultural contexts, and as an introduction to the world of cryptography. They remind us of the ongoing journey from simple historical encryption methods to the highly complex and secure systems that protect our digital world today. The future of these ciphers lies not in their practical application for security, but as essential educational and conceptual tools in the ever-expanding field of cryptography.